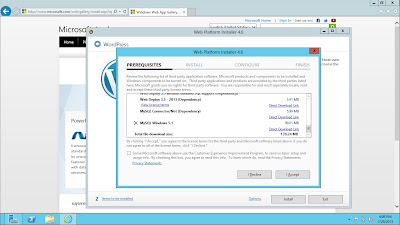
So lets look at the results from the TurnKey box using nmap:
nmap -A -sC
192.168.1.200 -oA ~/Desktop/wordpress/turnkey_nmap_init
Starting
Nmap 6.25 ( http://nmap.org ) at 2013-07-31 19:35 EDT
Nmap scan
report for 192.168.1.200
Host is up
(0.00047s latency).
Not shown:
997 closed ports
PORT STATE SERVICE VERSION
22/tcp open
ssh OpenSSH 5.5p1 Debian
6+squeeze3 (protocol 2.0)
|
ssh-hostkey: 1024 81:12:e6:73:39:90:78:d2:8b:30:57:85:42:dd:e3:0d (DSA)
|_2048
af:76:4b:f1:8f:cf:76:68:88:67:2c:3a:84:c7:8f:32 (RSA)
80/tcp open
http Apache httpd 2.2.16 ((Debian))
|_http-methods:
No Allow or Public header in OPTIONS response (status code 200)
|_http-title:
TurnKey LAMP
443/tcp
open ssl/http Apache httpd 2.2.16
((Debian))
|_http-methods:
No Allow or Public header in OPTIONS response (status code 200)
|_http-title:
TurnKey LAMP
| ssl-cert:
Subject: organizationName=TurnKey Linux
| Not valid
before: 2013-07-29T21:34:26+00:00
|_Not valid
after: 2023-07-27T21:34:26+00:00
|_ssl-date:
2013-07-31T23:36:15+00:00; 0s from local time.
MAC Address:
00:0C:29:F8:C7:0B (VMware)
No exact OS
matches for host (If you know what OS is running on it, see
http://nmap.org/submit/ ).
TCP/IP
fingerprint:
OS:SCAN(V=6.25%E=4%D=7/31%OT=22%CT=1%CU=35089%PV=Y%DS=1%DC=D%G=Y%M=000C29%T
OS:M=51F99F6F%P=i686-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=10C%TI=Z%CI=Z%II=I%T
OS:S=8)OPS(O1=M5B4ST11NW4%O2=M5B4ST11NW4%O3=M5B4NNT11NW4%O4=M5B4ST11NW4%O5=
OS:M5B4ST11NW4%O6=M5B4ST11)WIN(W1=16A0%W2=16A0%W3=16A0%W4=16A0%W5=16A0%W6=1
OS:6A0)ECN(R=Y%DF=Y%T=40%W=16D0%O=M5B4NNSNW4%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A
OS:=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%
OS:Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=
OS:A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=
OS:Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%
OS:T=40%CD=S)
Network
Distance: 1 hop
Service
Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.47 ms 192.168.1.200
OS and
Service detection performed. Please report any incorrect results at
http://nmap.org/submit/ .
Nmap done: 1
IP address (1 host up) scanned in 28.35 seconds
And the Windows host using nmap:
nmap -A -sC
192.168.1.9 -oA ~/Desktop/wordpress/iis_nmap_init
Starting
Nmap 6.25 ( http://nmap.org ) at 2013-07-31 19:37 EDT
Nmap scan
report for WIN-LFGTTR6DO5G.home (192.168.1.9)
Host is up
(0.0013s latency).
Not shown:
999 filtered ports
PORT STATE SERVICE VERSION
80/tcp
open http Microsoft IIS httpd 8.0
|
http-methods: Potentially risky methods: TRACE
|_See http://nmap.org/nsedoc/scripts/http-methods.html
|_http-title:
Microsoft Internet Information Services 8
MAC Address:
00:0C:29:78:F9:BA (VMware)
Warning:
OSScan results may be unreliable because we could not find at least 1 open and
1 closed port
Device type:
general purpose|phone
Running
(JUST GUESSING): Microsoft Windows 7|Phone|2008|Vista (93%)
OS CPE:
cpe:/o:microsoft:windows_7::-:professional cpe:/o:microsoft:windows
cpe:/o:microsoft:windows_server_2008::beta3 cpe:/o:microsoft:windows_vista::-
cpe:/o:microsoft:windows_vista::sp1
Aggressive
OS guesses: Microsoft Windows 7 Professional (93%), Microsoft Windows Phone 7.5
(92%), Microsoft Windows Server 2008 Beta 3 (92%), Microsoft Windows Vista SP0
or SP1, Windows Server 2008 SP1, or Windows 7 (92%), Microsoft Windows Vista
SP2, Windows 7 SP1, or Windows Server 2008 (92%), Microsoft Windows Vista Home
Premium SP1 (91%), Microsoft Windows Server 2008 SP1 (89%), Microsoft Windows
Vista SP0 - SP1 (86%)
No exact OS
matches for host (test conditions non-ideal).
Network
Distance: 1 hop
Service
Info: OS: Windows; CPE: cpe:/o:microsoft:windows
TRACEROUTE
HOP RTT ADDRESS
1 1.31 ms WIN-LFGTTR6DO5G.home (192.168.1.9)
OS and
Service detection performed. Please report any incorrect results at
http://nmap.org/submit/ .
Nmap done: 1
IP address (1 host up) scanned in 17.15 seconds
Let's review what the results are telling you first by looking at the TurnKey host:
It identified three ports running on the host: 22, 80, 443. This makes sense running a web server.
Nmap told me the versions of the software on those ports:
Port 22 is running OpenSSH 5.5p1
Port 80 & 443 is running Apache 2.2.16 with No
Allow or Public header in OPTIONS response
I'll use this information later to see if there are any exploits that are remote based. But first need to analyze the Windows Server.
Windows Server:
Nmap on identified one port open: 80.
Nmap on identified one port open: 80.
Port 80 is running Microsoft IIS httpd 8.0 with Potentially
risky methods: TRACE
This is it for today. Tomorrow will look at running Nikto to see if it identifies any default or identifiable files running on those servers.